December 24, 2023
Analysis and resolution of the “Searchie will damage your computer” alert on Mac
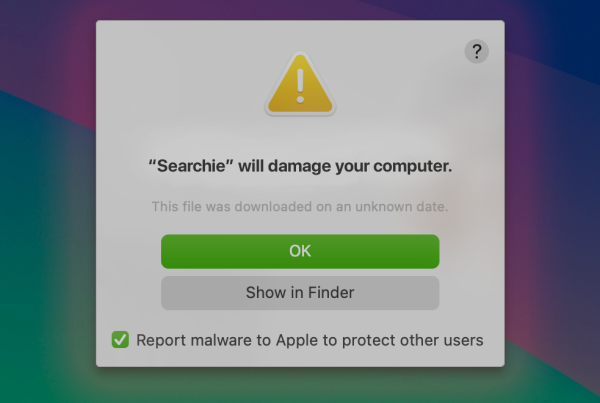
The "Searchie will damage your computer" alert represents a significant security notification emanating from macOS's Gatekeeper functionality. This alert signifies the detection of the Searchie process, a component frequently linked to adware threats. This alert transcends a simple warning, serving as a critical element of an advanced defense strategy, intricately crafted to protect the user's system's integrity and privacy. Upon…
Read More




