This macOS-platform threat can steal passwords, encrypt files, delete data, and install backdoors.
Researchers have discovered an updated version of the RustBucket malware that specifically targets macOS users. This version includes enhanced capabilities for stealthy system penetration and evasion of antivirus detection. Experts from Elastic Security Labs noted in their recently published report that this variant of RustBucket, part of the malware family targeting macOS systems, incorporates persistence features that were absent in previous versions. They also emphasize that the updated RustBucket employs a flexible network infrastructure strategy to effectively manage and coordinate its actions.
RustBucket is a toolkit developed by a North Korean cyber threat actor known as BlueNoroff and is associated with the Lazarus Group, an elite hacking group responsible for numerous cyber operations. Lazarus Group, in turn, operates under the control of North Korea’s key intelligence agency, the Reconnaissance General Bureau (RGB).
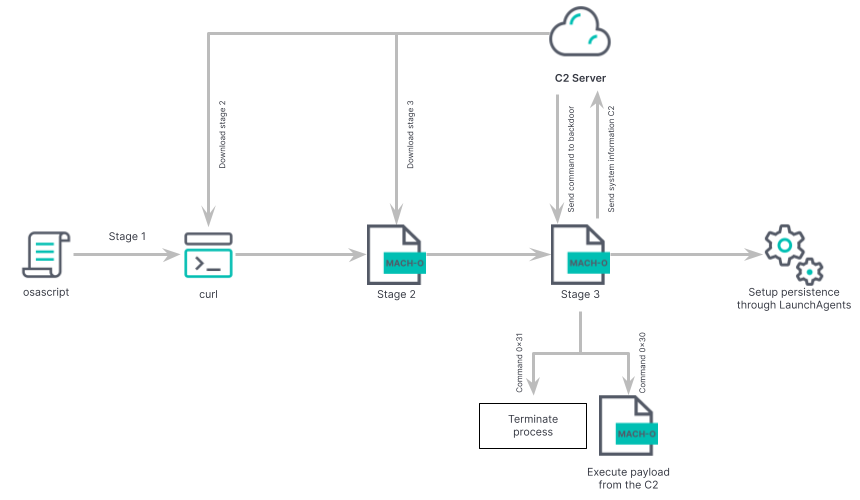
The malware was discovered in April 2023 when Jamf Threat Labs described it as an AppleScript-based backdoor capable of receiving secondary payloads from a remote server. The secondary malware, compiled in Swift, is designed to be downloaded from the command-and-control server of the primary RustBucket malware. It is a binary file based on Rust with extensive information-gathering capabilities, allowing it to acquire and execute additional Mach-O binary files or shells on compromised systems.
While this is the first instance of BlueNoroff malware specifically targeting macOS users, a version of RustBucket for .NET with a similar feature set has emerged in the wild. An analytical review of the RustBucket campaign conducted by the French cybersecurity company Sekoia in late May 2023 highlights the recent activity of the Bluenoroff hacking group and their use of cross-platform languages to develop malware. This approach is likely aimed at expanding their capabilities and increasing the number of potential victims.
The infection chain involves a macOS installer file that installs a fake but functional PDF reader. A significant aspect of the attack is that the malicious activity is triggered only when the infected PDF file is launched using the fake PDF reader. Initial entry vectors include phishing emails and the use of fake accounts on social networks. The observed attacks primarily target financial institutions in Asia, Europe, and the United States, indicating an intention to generate illicit profits by circumventing sanctions.
One remarkable characteristic of the recently discovered version is its uncommon way of staying active and its reliance on a dynamic DNS domain [docsend(dot)linkpc(dot)net] for command and control.
According to the researchers, the updated RustBucket sample establishes its own persistence by adding a plist file at the path: /Users/<user>/Library/LaunchAgents/com.apple.systemupdate.plist Additionally, it copies the malware binary file to the following path: /Users/<user>/Library/Metadata/System Update.